How HiScout Supports the Implementation of the NIS-2-Directive
The NIS-2-Directive does not determine a specific compliance framework. However, the requirements of the NIS-2 can be categorised in the NIST Cybersecurity Framework (2013). It covers the NIS-2 goals and is relevant for both – the IT and OT network environments. The NIST Cybersecurity Framework consists of five core functions, which are covered by IT-Basic Protection, ISO 27001 and BCM mapped in HiScout:
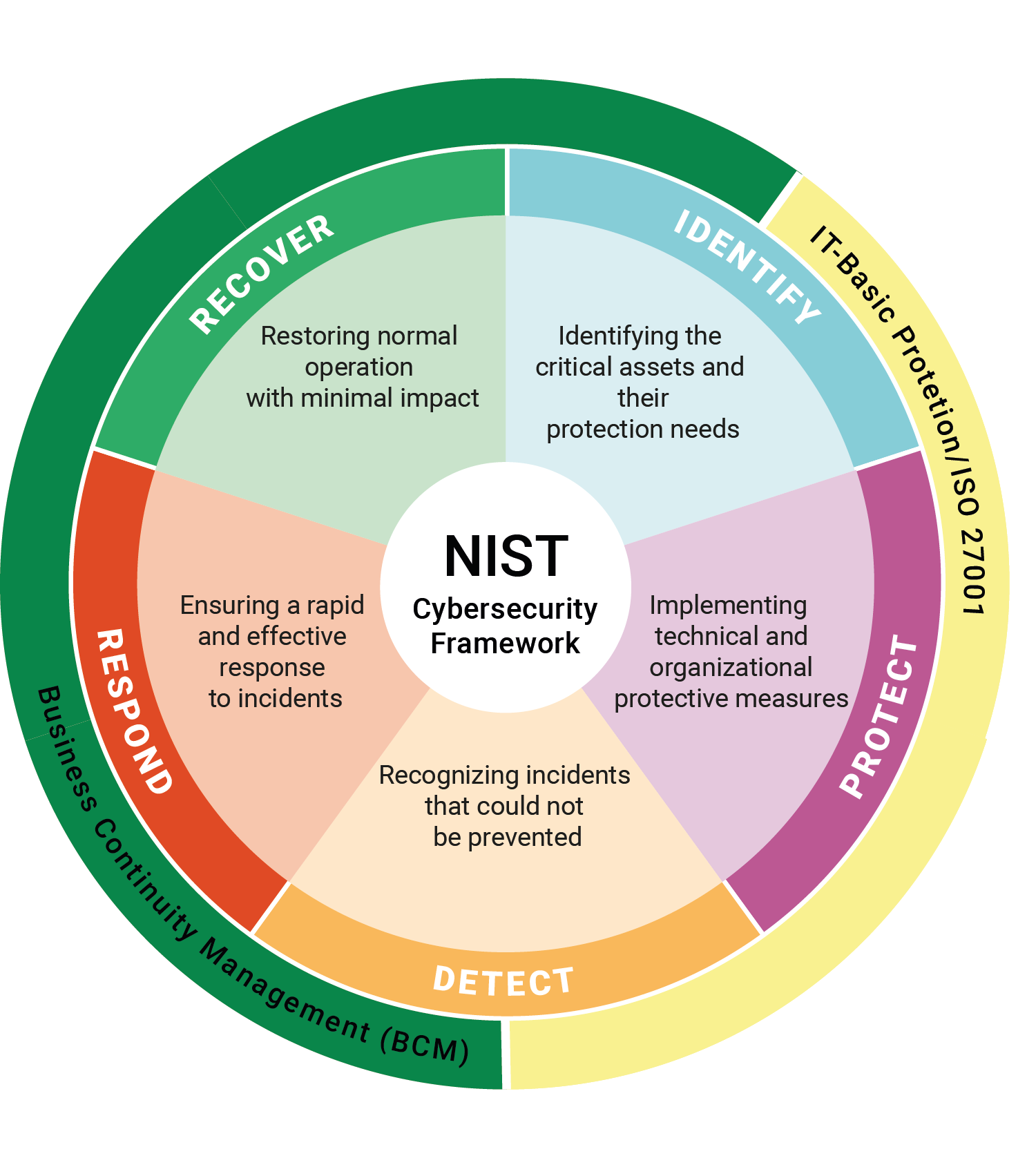
HiScout provides comprehensive support for fulfilling the NIS-2-Directive requirements and supports companies in increasing their IT security standards and complying with legal requirements. Our solutions cover the core requirements and offer extensive support for implementing NIS-2:
- Risk management and information system security: Determining protection needs and risk analysis for security evaluation
- Lifecycle management for the acquisition, development and maintenance of IT systems, components and processes
- Management of vulnerabilities and security measures
- Establishing a third-party risk management
- Developing a complete, comprehensible and scalable security control framework
- Overcoming security incidents through effective incident management, crisis management and emergency planning
- Maintaining Operations: Backup management and business continuity in case of an emergency situation and recovery after an incident
- Secured Emergency Communication: Managing emergency response Managing emergency response through trained crisis and emergency teams (BAO)
- Awareness: To be prepared for security incidents through training, exercises and tests
With HiScout, you are fully equipped to fulfil the NIS-2 requirements and maximise your IT security.
Learn more about the NIS-2-Directive
and its Implementation in HiScout
Blog
Find out more about the NIS-2-Directive and how you can implement it with HiScout in a structured manner, in our blog.
read NIS-2 Blog
Webinar
You can find our latest video on the NIS-2-Directive and its implementation in HiScout on our YouTube channel.


