HiScout Client Backup
Highest Level Data Backup
Data is a valuable asset in today’s digital world. With HiScout Client Backup, you ensure the security and availability of your data – whether it is protection against cyberattacks, human errors or technical failures. Our powerful add-on provides targeted data backup for individual clients and ensures fast recovery when required.

Product Data Sheet
Find all essential information on the HiScout Client Backup add-on here.
Request Product Data SheetIntroduction
Would you like to know more about implementing HiScout in your organisation?
Contact FormSome of the countless reasons how you can significantly benefit by using HiScout Client Backup
Our solution allows you to benefit from a flexible and reliable backup strategy that integrates seamlessly into your existing IT landscape.
Targeted Client Backup: Save and recover individual clients without affecting other data.
- Efficient recovery: Reduce downtime with a fast and reliable recovery function.
- Automated processes: Schedule backups and intelligent versioning for transparent data security.
- Granular control: Flexible import and export options for individual backup requirements.
- Offline availability: Protect your data independent of online systems.
- Integrated security mechanisms: Compatible with existing security and compliance policies.
HiScout Client Backup is suitable for companies of all sizes which want to efficiently safeguard their Governance, Risk & Compliance (GRC) processes. Industries with high data protection requirements – such as financial service providers, health care, or public administration – in particular, benefit from this solution.
HiScout Partners
Depending on the needs of our customers, we work together with qualified partner companies to provide specialist advice on setting up management systems and launching HiScout modules in the organisation. We offer regular further training and individual support to continuously ensure HiScout’s high quality standards.


Materna is an IT service provider operating on an international scale. It offers the launch and optimisation of information security management systems in the area of cybersecurity, based on ISO 27001, BSI IT-Basic Protection or ISIS12. Other topics include Security Operations Centres, Security Awareness, Vulnerability Management and IAM. We have been successfully supporting large organisations together as partners for the past several years. Materna offers our complete service portfolio including customising and hosting.
www.materna.de/cybersecurity
secunet Security Networks AG offers cybersecurity for public authorities and companies. With a combination of products and consulting, it ensures resilient digital infrastructures and the highest possible level of protection of data, applications and digital identities. secunet thereby specialises in areas where special security requirements are needed – such as Cloud, IIoT, eGovernment and eHealth. HiScout and secunet jointly support numerous organisations in the public sector at state and federal level.
www.secunet.com
InfoGuard AG specialises in cyber security, information security and IT security. Our exclusive partner in Switzerland supports our customers in the areas of information security management, data protection, governance-, risk- and compliance management, as well as business continuity management. This also includes customising individual solutions.
www.infoguard.ch
Bechtle is the largest German IT system house and one of the leading IT providers in Europe. Bechtle offers a complete, seamless cross-vendor range of IT infrastructure and IT operational services to its customers from industry and commerce, the public sector and the financial market from a single source. This also includes consulting and software implementation for managing data protection and information security. Together, we manage framework agreements for software procurement in public institutions.
www.bechtle.com
Computacenter AG & Co. oHG is a provider of IT strategy consulting as well as IT infrastructure implementation and management. Their services range from consulting and support in setting up an information security management system, up to the certification in accordance with ISO 27001 or BSI IT-Basic Protection.
www.computacenter.com/de
HiSolutions AG is one of the leading consulting firms for IT security and IT management in German-speaking areas. HiSolutions has been supporting customers in nearly all business sectors for the past 30 years. HiSolutions and HiScout work together closely on product specifications, and jointly support numerous companies in the banking and insurance sectors. HiScout is a spin-off of HiSolutions AG, however, both companies operate independent of each other.
www.hisolutions.com
The Ostwestfalen-Lippe IT (OWL-IT) sees itself as an innovative service company that enhances the efficiency of municipalities by providing secure IT infrastructure, modern technology, and specialized software. As a municipal IT service provider, it directly and indirectly serves around 9 million residents in North Rhine-Westphalia with its services. It was the first municipal service provider to be certified by the German Federal Office for Information Security (BSI) according to IT baseline protection standards. Targeted IT solutions, dynamic innovations, trusted collaboration, and extensive expertise—that’s OWL-IT.
www.owl-it.de
Sopra Steria is a leading European technology company renowned for its expertise in the fields of consulting, digital services and software development. The group supports its clients in driving digital transformation forward and achieving tangible and sustainable results with comprehensive end-to-end solutions that help companies and public authorities become more competitive and efficient. Sopra Steria is one of HiScout’s first partners. It offers tremendous know-how in the application of HiScout Basic Protection.
www.soprasteria.de
telent GmbH offers tailor-made technology solutions and services in the areas of critical infrastructures (KRITIS), digitalisation and Industry 4.0. When it comes to networking and automating digital business processes, telent primarily places great emphasis on comprehensive expertise in the areas of cybersecurity, technology and infrastructure services. We have been jointly advising our customers in the area of integrated management systems for several years.
www.telent.de TÜV NORD IT Secure Communications advises customers in their efforts to strengthen trust in robust, high availability IT infrastructures and organisations and supports client on their path to secure digital transformation. Founded in Berlin in 2018, the company specialises in consulting services in the areas of information technologies and telecommunications. Together with HiScout, NORD IT Secure Communications supports in the launch of management systems for information security, data protection and business continuity management.
TÜV NORD IT Secure Communications advises customers in their efforts to strengthen trust in robust, high availability IT infrastructures and organisations and supports client on their path to secure digital transformation. Founded in Berlin in 2018, the company specialises in consulting services in the areas of information technologies and telecommunications. Together with HiScout, NORD IT Secure Communications supports in the launch of management systems for information security, data protection and business continuity management.

KIK-S GmbH (Kommunale IT-Kooperation Stadtwerke) (Municipal IT Cooperation for Municipal Utilities) specialises in consulting, project management, process and IT management including operation for critical infrastructures operators. Together with SEPRO Consulting, it supports municipal utilities in particular with the launch and operation of their ISMS. With their HiScout-based Software-as-a-Service (SaaS) solution ISMS4energy, KIK-S and SEPRO Consulting are leaders in the implementation and operation of an ISMS for municipal utilities. SEPRO Consulting provides customers with expert technical support.
 Benefit from the unique combination of PwC’s professional expertise and the technological capabilities of its partners. Together, we effectively and efficiently support you and your company on your path to IT security and compliance. Thanks to close partnerships with leading technology providers, we find the optimal solution for your company and guide you through the entire process. Together, we shape your path to the future.
Benefit from the unique combination of PwC’s professional expertise and the technological capabilities of its partners. Together, we effectively and efficiently support you and your company on your path to IT security and compliance. Thanks to close partnerships with leading technology providers, we find the optimal solution for your company and guide you through the entire process. Together, we shape your path to the future.
 Intelli Systems offers intelligent solutions for robust IT governance, risk management, compliance, and information security. The goal is to help companies implement effective IT governance, minimize risks, and ensure regulatory compliance. Intelli Systems supports you in strengthening your information security to protect sensitive data and secure your business operations.
Intelli Systems offers intelligent solutions for robust IT governance, risk management, compliance, and information security. The goal is to help companies implement effective IT governance, minimize risks, and ensure regulatory compliance. Intelli Systems supports you in strengthening your information security to protect sensitive data and secure your business operations.
 HUG GmbH are experts in the practical implementation of regulatory requirements. With strategic thinking and entrepreneurial pragmatism, it has established itself as one of the leading consulting firms in the areas of auditing and consulting for regulated companies. In the area of audit, they work for the internal audit departments of banks, insurance companies, financial institutions and corporations. Its consulting activities include information security, IT management, project management and certification preparation.
HUG GmbH are experts in the practical implementation of regulatory requirements. With strategic thinking and entrepreneurial pragmatism, it has established itself as one of the leading consulting firms in the areas of auditing and consulting for regulated companies. In the area of audit, they work for the internal audit departments of banks, insurance companies, financial institutions and corporations. Its consulting activities include information security, IT management, project management and certification preparation.
 The combination of IT services and information security is neam’s strength – and has been for almost 30 years. With more than 120 highly qualified IT professionals, they work for their customers both nationally and internationally. They are ISO 9001 and 27001 certified. Their Service & Support solutions give you all the benefits of a professional IT department. Whether on-prem, hybrid or in the cloud – the high-performance consulting, technology & support team is there for you.
The combination of IT services and information security is neam’s strength – and has been for almost 30 years. With more than 120 highly qualified IT professionals, they work for their customers both nationally and internationally. They are ISO 9001 and 27001 certified. Their Service & Support solutions give you all the benefits of a professional IT department. Whether on-prem, hybrid or in the cloud – the high-performance consulting, technology & support team is there for you.

Quality
HiScout partners are specialists in all topics relating to Governance Risk & Compliance and regularly participate in our on-going training programmes.
Industry expertise
Take advantage of the long years of experience and specialised industry knowledge of our partners to implement your individual requirements optimally.
Trust
A long-standing and trusting relationship connects us to many partners and customers. We work together on optimising and integrating your management systems.
HiScout ADConnect
Maximum efficiency through
automated user administration
With HiScout ADConnect, you can automate your user administration, minimise potential errors and create a lean, secure and constantly up-to-date user structure – without any manual effort. Thanks to flexible configuration options, the synchronization between Active Directory and HiScout adapts precisely to your individual requirements.
Make your identity and authorisation management future-proof, to obtain maximum productivity, less administrative efforts and a quick Return on Investment (ROI).

Seamless Integration
ADConnect is a Lightweight Directory Access Protocol (LDAP) interface that ensures automatic synchronisation of user and group information from the Active Directory. Changes in the user structure are regularly and reliably transferred to HiScout– without any manual effort.
Optimisation through Automation
- Minimisation of manual maintenance errors
- Time and cost savings due to reduced administrative effort
- Automatic updating of user rights and groups
Individual Customisation
Flexible configuration options enable precise adaptation to your specific requirements and perfect integration into your IT landscape. Define individual synchronisation rules and maintain full control over your user administration.
Increased Security
- Automatic updating of user rights and group affiliations
- Identification and administration of inactive or unused accounts
- Improved security and compliance for your organisation
Flexible and Automated User and Group Affiliations
User Management
- Default status of new users: Define the status of new users (e.g. portal user, non-portal user, unknown user).
- Management of inactive users: Set rules for handling inactive users.
- Exception handling: Individual control over how specific users should be handled (deactivate, delete or ignore).
- Automatic reassignment of persons to a different group: Reassignment of persons to a different group based on AD groups.
AD Group Administration
- Group reset: Option to reset user groups.
- Status adaption of AD groups: Transfer of status values to new or existing users.
- Default category for AD groups configured incorrectly: Automatic assignment of groups configured incorrectly
Additional Functions
- Support for multiple sub-domains
- Individual assignment of categories for new users
- Interception of misconfigurations with predefined default values
- Default values can be defined for unset values
Facilitate your user administration with the HiScout ADConnect Synchronisation add-on!
Save time and money, minimise administrative effort and increase security – all thanks to the automated and flexible user administration.
Product Data Sheet
Find all essential information on the HiScout ADConnect add-on here.
Request Product Data SheetIntroduction
Would you like to know more about implementing HiScout in your organisation?
Contact FormUser-Friendliness and Easy Integration
Intuitive Setup and Administration
HiScout ADConnect has been developed for ease-of-use. The user-friendly interface allows for a quick configuration, without having to acquire in-depth IT expertise. Clearly structured menus and easy-to-comprehend settings allow administrators to adapt the synchronisation to their individual requirements and manage it efficiently.
Perfect Integration into your Existing IT Landscape
ADConnect is seamlessly compatible with existing IT- and security policies and can easily be integrated into your existing system landscape. It supports multiple sub-domains, can be adapted to specific authorisation models and allows for a smooth collaboration with other IT systems. This ensures that your user and group administration continuously remains efficient and secure.
Are you Ready for the NIS-2-Directive?
Achieve Maximum IT-Security
and Compliance with HiScout

How HiScout Supports the Implementation of the NIS-2-Directive
The NIS-2-Directive does not determine a specific compliance framework. However, the requirements of the NIS-2 can be categorised in the NIST Cybersecurity Framework (2013). It covers the NIS-2 goals and is relevant for both – the IT and OT network environments. The NIST Cybersecurity Framework consists of five core functions, which are covered by IT-Basic Protection, ISO 27001 and BCM mapped in HiScout:
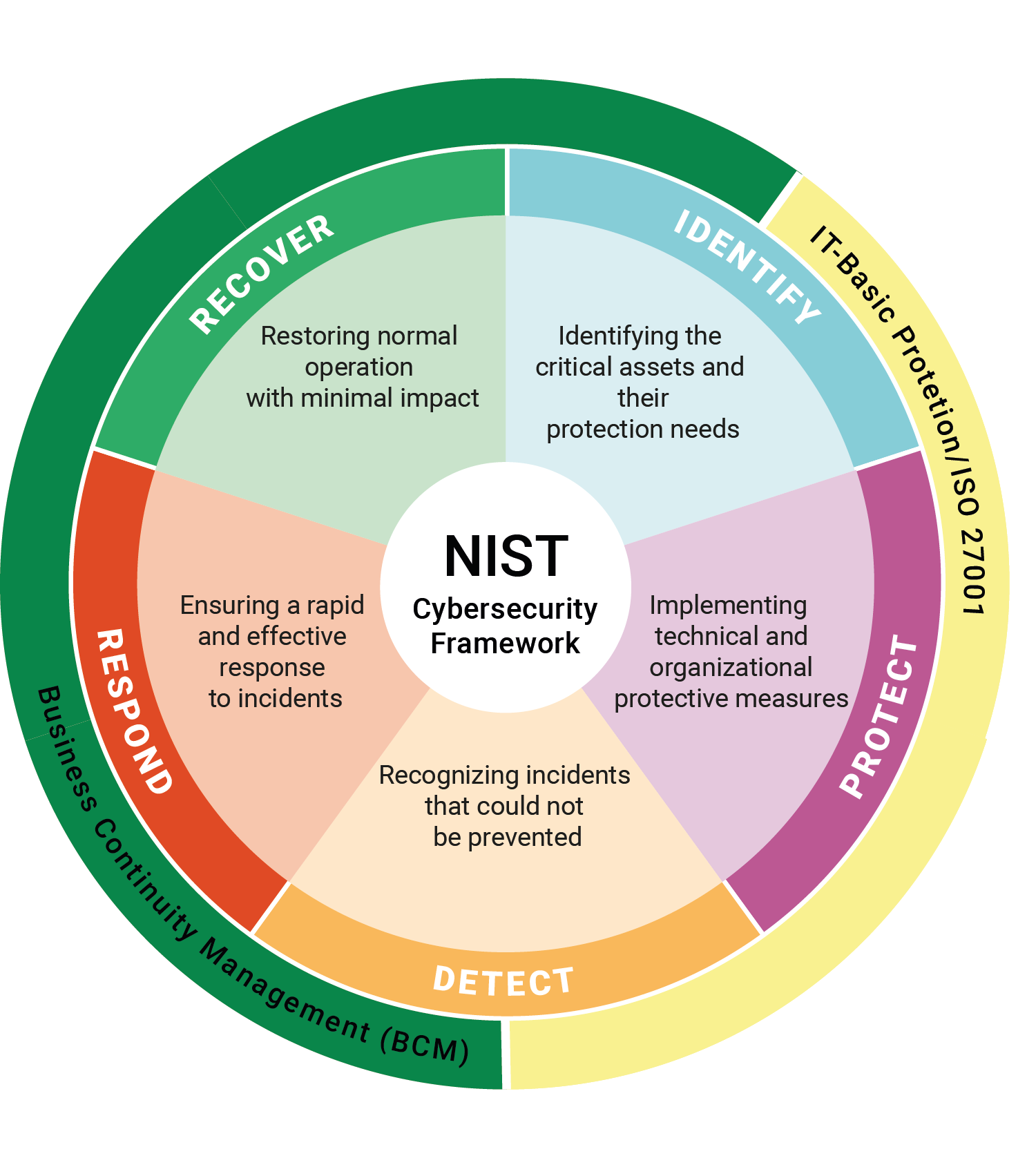
HiScout provides comprehensive support for fulfilling the NIS-2-Directive requirements and supports companies in increasing their IT security standards and complying with legal requirements. Our solutions cover the core requirements and offer extensive support for implementing NIS-2:
- Risk management and information system security: Determining protection needs and risk analysis for security evaluation
- Lifecycle management for the acquisition, development and maintenance of IT systems, components and processes
- Management of vulnerabilities and security measures
- Establishing a third-party risk management
- Developing a complete, comprehensible and scalable security control framework
- Overcoming security incidents through effective incident management, crisis management and emergency planning
- Maintaining Operations: Backup management and business continuity in case of an emergency situation and recovery after an incident
- Secured Emergency Communication: Managing emergency response Managing emergency response through trained crisis and emergency teams (BAO)
- Awareness: To be prepared for security incidents through training, exercises and tests
With HiScout, you are fully equipped to fulfil the NIS-2 requirements and maximise your IT security.
Learn more about the NIS-2-Directive
and its Implementation in HiScout
Blog
Find out more about the NIS-2-Directive and how you can implement it with HiScout in a structured manner, in our blog.
read NIS-2 Blog
Webinar
You can find our latest video on the NIS-2-Directive and its implementation in HiScout on our YouTube channel.
HiScout Plattform Version 3.11.3
Die Updates der HiScout Plattform können über ein einfaches Setup normalerweise eigenständig von einem Systemadministrator durchgeführt werden.

Update Ihrer HiScout Plattform
HiScout Master Release 3.7.0
HiScout-Updates bestehen aus zwei Komponenten, einem Plattform-Update mit den technischen Grundlagen für die Nutzung der HiScout-Module und einem Master-Update mit Aktualisierungen der HiScout Fachmodule.
Bei einem Update älteren Master-Versionen müssen alle Zwischenversionen installiert werden. Für die Installation des HiScout Master 3.7.0 ist die vorherige Anhebung der Plattform auf Version 4.0.0 notwendig.

Plattform-Updates
Plattform-Updates können über ein einfaches Setup normalerweise eigenständig von einem Systemadministrator durchgeführt werden.
Master-Updates
Master-Updates bedürfen manueller Konfigurationsarbeiten, weil neue Oberflächen, Workflows und Reports importiert werden. Ab der HiScout Master-Version 3.0.1 kann die Installation durch ein automatisiertes Staging per Skript unterstützt werden. Der Dienstleistungsaufwand für die Durchführung des automatisierten Stagings beträgt je nach Umfang und Stand Ihrer HiScout-Version 2 bis 5 Personentage.
Bei HiScout-Systemen mit kundenspezifischem Customizing kann ein Gesamtaufwand von bis zu 12 Personentagen entstehen.
Aktualisierung des BSI IT-Grundschutz-Kompendiums
Seit Februar 2023 steht das aktuelle IT-Grundschutzkompendium des BSI für HiScout zur Verfügung. Dieses können Sie jederzeit bei uns abrufen und als berechtigter HiScout-Administrator installieren.
Update Ihrer HiScout-Version
HiScout Basic Protection
IT-Basic Protection-Tool and Risk Analysis in Accordance with BSI 200-1, 200-2 and 200-3
The HiScout Basic Protection module fully complies with procedures in the BSI standards 200-1, 200-2 and 200-3. The market-forming basic protection tool for federal authorities, state administrations and operators of critical infrastructures (KRITIS) aligns exactly with the BSI procedures. Therefore, it easily records existing data from other tools – such as GSTOOL. Users are safely guided through all phases of the implementation of basic protection – from defining the information network, to the submission of the certification documents. Elements such as components, threats, measures and processes can be easily adapted to your own basic protection procedures, without having to do any sort of programming.
HiScout Basic Protection based standard solutions are available to the federal authorities via HiScout’s standard solution ZeDIS. This is provided as a Service Solution (SaaS) via the Federal Information Technology Centre (ITZBund).
Get to know more about HiScout Basic Protection in the Webinar

Newsletter
Exciting news and interesting facts on HiScout products and topics
Sign up for NewsletterImportant Dates
Important industry events, HiScout webinars and online seminars at a glance
To OverviewMagazine
Read all our HiScout articles, publications and press releases
(available only in German language)
Step-by-step to certified IT-Basic Protection
-
Hierarchical information networks and security concepts
First of all, all the components which are relevant to the IT-basic protection of the information networks such as processes, applications, IT systems, industrial control systems networks, locations and generic aspects, are defined. The networks can be arranged and evaluated hierarchically. Each level can represent a different issue e.g. processes and procedures, security concepts and organisational structures. Each hierarchy can be evaluated separately, e.g. in order to create an overview of all security concepts at the Berlin site.
-
Structural analysis with centralised and decentralised target objects
In the structural analysis, all components of the information networks and processes, as well as security concepts are recorded and linked in their mutual dependencies. Assets or complete networks can be made available as a service or basic service in large organisations with distributed working. Sub-organisations can book these services, link them to their own security concept and use them as an own target object, with the stored level of protection. The responsibility for the basic protection check- and risk analysis lies with the provider; redundancies in security concepts are avoided.
-
Assessment of protection requirements with automatic inheritance
HiScout focuses on the information to be protected and inherits the identified protection requirements alongside the IT structure, in accordance with the individual target objects. It thereby considers the individual target objects that observe the cumulative effects which occur.
The mandatory protection requirements are compared to the agreed protection in case of offered or purchased services, in order to disclose any gaps in the protection coverage. Inheritance paths and origin are displayed transparently for each target object.
Protection requirements, protection requirement classes, damage scenarios and other parameters can be individually customised. -
Automatic modelling in accordance with IT-Basic Protection
Relevant security requirements of the target objects are determined during modelling. This is required in order to evaluate the security of existing processes as well as those in the planning stage. BSI Basic Protection Compendiums and individual components can be maintained and modelled in HiScout Basic Protection. You can also store your own standard modellings for freely-definable target object types and automatically apply them.
-
Basic Protection check with the Questionnaire function
The individual security requirements of the basic protection components are automatically taken over. A tabular overview with graphical display shows the progress of the basic protection, core protection and standard protection and provides a quick overview of all modelled requirements of the basic protection compendium. Existing basic protection checks are integrated automatically or manually, as required. The implementation status for requirements, target object and network are clearly documented in a reporting.
-
Risk analysis with action plan
The HiScout risk analysis is carried out in three steps – risk overview, risk classification and risk treatment. The threats can be taken from the existing components and be enhanced manually. Using a risk matrix, the gross and net risk per hazard is automatically calculated based on the frequency of occurrence and impact. The evaluation levels and the resulting risk classes can be freely adapted to the requirements of the respective organisation. The implementation status of the measures is displayed transparently in the target objects and can be incorporated into the risk assessment. The measures are transferred to the basic protection check after the approval of the risk action plan. Risk analyses, which are no longer valid, are archived for future checks. The HiScout risk analyses fulfils the requirements for BSI standards 200-3 and 100-3, including suggested measures based on the cross-reference tables for the IT-Basic Protection Compendium.
-
Certifiable reference reports
The reference documents A1-A6, based on BSI standard 200-2, are created at the touch of a button and are immediately available for download. All reports can be customised according to individual specifications and company design if Customizing has been commissioned. The HiScout live reports are automatically displayed and updated.
A data pool for basic protection, data protection and risk management
The HiScout Data Protection can be extended to an integrated management system with a common database. A beautiful example of the interaction of the HiScout Basic Protection, HiScout Data Protection, HiScout ISM und HiScout BCM modules: the basic protector becomes active and surveys the processes as well as the required applications. The Emergency Manager is delighted with the collected data and uses it for the Business Impact Analysis. Meanwhile, in the directory of the processing activities, the data protector uses the currently maintained master data to record what data is processed by which application. The basic data protector can incorporate this information into its process analysis to assess the protection requirements.
HiScout technology can be upgraded and is future-proof
The HiScout GRC software is a browser-based multi-user application, which does not require any installation on the client-side. 100% of the development and support are carried out in Germany. The data model and user interfaces of the HiScout platform can be upgraded and expanded at any time without requiring programming skills, in order to realize individual requirements of our clients. We are in regular dialog with our user groups and stakeholder forums, and jointly align our development goals with practical needs and future requirements. HiScout Data Protection can be combined with other HiScout add-ons such as HiScout Questionnaire, HiScout Business Logic Engine, HiScout DataExchange and HiScout DocGen to include customized processes, questionnaires, workflows, reports and database connections.
Product data sheet
Find all essential information on the HiScout Basic Protection module here.
Request Now!Synergies
A software for different management systems which saves time and effort.
Work more efficientlyHiScout ISM
Software for Information Security Management (ISM) in accordance with ISO 27001/2
With HiScout ISM, you gain access to a powerful software, which makes your Information Security Management System (ISMS) efficient and future-proof. Developed in accordance with the specifications of the international ISO 27001 series of standards, HiScout helps companies to optimise their security processes, meet compliance requirements – including new regulatory requirements such as NIS 2 and DORA – and easily obtain certifications. Thanks to intelligent automation, you minimize the effort required for reoccurring tasks, while a dashboard bar shows the current implementation status of the ISMS at a glance. This allows you to continuously maintain an overview of your security strategy.

Efficient ISMS-Management with HiScout ISM
With HiScout ISM, you can master the current and future information security requirements in compliance with the current standards efficiently. From comprehensive risk analysis to outsourcing management – benefit from the comprehensive features that strengthen your ISO 27001-compliance in a sustainable manner, and optimise your security processes.
Additional Functions
- Customisable risk management with optional web-based questionnaire query
- Comprehensive asset management with protection requirement assessments and inheritance
- Monitoring and documentation of security measures
- Support for common standards norms (ISO 27001/2, BSI IT- Basic Protection, COBIT, NIS-2, DORA) as well as customer-specific compliance requirements
- Audit-proof document management with historization and versioning
- Standardised processing of security incidents
- Administration of external audits and executing self-assessments
- Extensive reporting and generating reports with the touch of a button
- Client management with preconfigured authorisation system
ISM Tool for Large Organisations with Individual Requirements
Individual work areas and evaluations
Customise the user interface of the HiScout ISMS software for specific tasks quickly and easily, and distribute these via a direct link to the persons-in-charge. Define any tabular evaluations of the data and make them available in Excel format or via a link.
Use in highly regulated and critical environments
Versioning, historization and individual release processes ensure that the change history in the HiScout ISMS tool is fully traceable and audit-proof. The HiScout authorisation system, with comprehensive roles- and rights control, protects your data from unauthorised access.
Client administration with a pre-configured authorisation system
HiScout Client Management is successfully used in complex organisations with numerous independent sub-units. Individually determine whether the data from your ISMS is to be used generically or only client-based. Clients and authorisations can be administered centrally or de-centrally and can be set up automatically. The maintenance of the Guidelines & Statements of Applicability is carried out for more flexibility and clear division of client-based areas of responsibility.
Newsletter
Exciting news and interesting facts on HiScout products and topics
Sign up for NewsletterImportant Dates
Important industry events, HiScout webinars and online seminars at a glance
To OverviewMapping and automation of individual security processes
Data collection using online questionnaires
Data for the central information security management system is collected from employees and service providers directly on-site in an automated process, and read-into the HiScout database after verification. You can create your own questionnaires with the HiScout Questionnaire add-on.
Automated security processes
Security incidents, risk analysis, protection requirement assessments, and tracking of measures can be supported via automated processes. Internal and external stakeholders are actively notified. You can define your own workflows with the HiScout Business Logic Engine.
Seamless integration in to the existing tool landscape
Incoming and outgoing interfaces of HiScout DataExchange merge data from different systems and ensure high data quality.
Role and process-focused reporting
Integrated live reporting for each work step provides the persons-in-charge with the latest information. You can create your own management reports with HiScout DocGen.
Additional wealth of knowledge thanks to the BSI-Basic Protection-Compendium
The HiScout ISMS tool contains the full functional range of the HiScout Basic Protection module and the current IT Basic-Protection-Compendium of the German Federal Office for Information Technology Security (Bundesamt für Sicherheit in der Informationstechnik or BSI). The basic protection modules are available to you as reference. In risk analysis, you can directly take over the threats and security measures stored in BSI.
ISMS tool for KRITIS
In cooperation with SEPRO Consulting and KIK-S, we have especially put together an offer for energy suppliers having operators of critical infrastructures. Click on ISMS4Energy for more information.
ISMS – Setup and certification of your information security management system in the PDCA cycle
The HiScout ISMS software supports you throughout the entire PDCA cycle. Your Information Security Management System (ISMS) must constantly be adapted to the changing processes within the organisation – including the new technology, newly discovered weak points and new legal conditions. The PDCA cycle, which originates from Quality Management is, according to William Edwards Deming, an established procedure to set up management systems and continuously improve them.
-
PLAN –Taking stock, defining goals and action planning
Management system basics
Store all sets of rules and regulations, the specifications agreed upon contractually and individual industry norms (e.g. SOX, Euro-SOX and BAIT) in one system. Central norms such as ISO 2700X and COBIT are regularly updated. Administer your company’s entire IT security organisation, process descriptions and meetings. -
DO – Implementation of the measures
Master data management and determining protection needs
Record and maintain your assets such as IT systems, applications, services and external service providers, as well as their logical and technical connections and dependencies. Determine the protection needs of the assets from the perspective of those responsible and have them passed on automatically along the recorded structures.Risk analysis and action planning
Risk analysis can be carried out according to common market standards such as ISO 27005, ISO 31000 or BSI 200-3, and can be adapted to individual needs. Classify the hazards into risk classes by specifying their probability of occurrence and amount of damage. Assign threats to the target objects. Then plan the necessary security measures, including expenses for integrated cost planning.Action management
For generic processes, the implementation of security measures is documented in the central action management via tracking and reporting. Role-based work areas, predefined workflows and automatic notifications, (e.g. for expiring implementation deadlines) help you in ensuring that the processing is reliable and time saving. Get a quick overview on the current status of the management system at any time.Handling security incidents
The control and documentation of security incidents runs in a fully standardised manner with HiScout, and is fully transparent. -
CHECK – Success control and monitoring goal-attainment
External audits and self-assessments
HiScout maps the entire audit and self-assessment process – from planning content and criteria, to recording the degree of fulfilment and any deviations – up to their treatment through measures. Clear and management-friendly reports of the entire audit process are created at the touch of a button. You can carry out the data collection de-centrally and automatically in HTML or PDF format with the questionnaire function in HiScout Questionnaire. -
ACT – Elimination of deficiencies and improvements
The cycle starts anew
Thanks to the high level of flexibility and adaptability of HiScout, continuous improvements in your procedures and security processes are quickly stored in HiScout. In contrast to statically implemented tools, you can carry out these changes economically and without programming efforts.
Product Sheet
You will find all the essential information on the HiScout ISM module here.
Request Now!Synergies
A common software for different management systems – saves time and effort.
Work more efficiently!HiScout Data Protection
Software for data protection management in accordance with EU GDPR (EU General Data Protection Regulation)
You can set up a legally compliant data protection management system for your organisation with HiScout Data Protection in a short period of time. You will be guided through all data protection topics step by step – from creating the processing directory to the deletion concept and the management of data protection incidents even if you are not a data protection expert. Evidence and documentation of your previous data protection tools can be uploaded in HiScout as applicable documents, to ensure a seamless transition. All reports required by you to fulfil the burden-of-proof in accordance with EU-GDPR (General Data Protection Regulation), are automatically generated. The HiScout dashboard, with clear graphics and diagrams, provides a quick overview of the current situation at all times.

Convenient data collection at the place of processing
The HiScout Questionnaire templates support you in surveying employees and external service providers via the processing activities carried out by you, or for which you are responsible. The questionnaires are sent, checked and read into the HiScout database through an automated process. A questionnaire for recording processing activities is included in the scope of delivery. You can create your own questionnaires with the HiScout Questionnaire add-on.
Using the standard data protection model
The use of the Standard Data Protection Model (SDM) is recommended by the Data Protection Conference and is mandatory for basic protection. With this method, you ensure that personal data processed in your organisation complies with the data protection regulations. It not only considers the risks of those effected, but also the risks for your organisation.
Safeguarding the rights of persons and parties concerned
The data protection module offers predefined processes for compliance and audit-proof documentation of the rights of persons and parties concerned to deletion, information, data transfer and correction.
Secure handling of data protection incidents
The HiScout process for handling data protection incidents helps you in recording data correctly and tracking data protection breaches. You keep track of the strict reporting deadlines to authorities and those concerned, and assign appropriate measures. Stored time stamps prove that the incident was handled in a GDPR (General Data Protection Regulation) compliant manner.
Multi-client capability at the highest level
Large organisations and consulting firms can manage hierarchical structures with clients and sub-clients in a single HiScout instance. The data can be used generically, as well as client-based. The HiScout authorisation system protects against unauthorised access and guarantees the data sovereignty and confidentiality of the clients.
Newsletter
Exciting news and interesting facts on HiScout products and topics
Sign up for NewsletterImportant Dates
Important industry events, HiScout webinars and online seminars at a glance
To OverviewStep-by-step to legally compliant data protection management
-
Directory of the Processing Activities
You describe all activities occurring in your organisation where personal data (PD) is processed, in the processing activities registry (VVT). The VVT is a mandatory data protection document which complies with GDPR (General Data Protection Regulation), and is the basis for all further activities when creating a data protection management system. It contains the following information:
- Data protection officer and person responsible
- Purpose and legal basis of processing
- Type of data recorded and transmitted
- Data flow with data origin and data recipient
- Data-bearing documents, applications and systems,
- Transferring data to non-EU countries
- Assignment of legal retention periods
- Authorisation groups
- Technical and organizational measures
- Other accompanying documents
-
Privacy Impact Assessment (PIA)
A protection impact assessment with threshold analysis shows whether a Privacy Impact Assessment (PIA) is required. The protection requirement assessment includes a detailed description of the processing, the processed data, the recognised risks and the selected risk-reduction measures. The remaining risks of the processing activity for those affected will be examined, in case a Privacy Impact Assessment (PIA) is required. The PIA in HiScout covers all important areas required by GDPR (General Data Protection Regulation) – the description of the processing activities, weighing the purpose of the processing as opposed to the intervention of the rights of those affected, and the assessment of the residual risks of those affected after the use of minimised measures. Finally, the data protection expert assesses whether the processing activity is still permissible.
-
Deletion Concept
The HiScout Data Protection module supports you in administering and carrying out the deletion procedure in accordance with GDPR (General Data Protection Regulation), and in recording the retention periods and legal basis. Existing deletion concepts and other accompanying documents can be embedded. The data stored in the processing directories are automatically prepared and are compiled into a report at the touch of a button in HiScout Version 3.1.2 and higher.
-
Technical and Organisational Measures
To ensure secure processing, all organisations which use personal data must define and document technical and organisational measures (TOMs) in accordance with GDPR (General Data Protection Regulation). HiScout allows you to select the measures from all catalogues stored in the program as well as your own measures maintained in other modules. You can then assign these to a processing activity, e.g., from the BSI Basic Protection Catalogue or various compliance guidelines, as well as from the standard data protection module.
-
Order Processing Contracts
An order processing contract must be concluded in case personal data is processed in a specific order. HiScout Data Protection offers the following options for mapping order processing conditions in HiScout Version 3.1.2 and higher:
- Recording of the order processing conditions with the client and subcontractor
- Assigned repository of the order processing contract
- Issuing an extract from the VVT with assigned TOMS as proof for the person responsible on the client-side
- Required notifications of deletions and changes for subordinated contractors
-
Transfer Impact Assessment
In order to comply with the new SCC (Standard Contractual Clauses) published by the EU Commission in 2021, a separate risk assessment must be carried out for data transfer to third countries. HiScout Data Protection supports you in carrying out the transfer impact assessment.
A data pool for basic protection, data protection and risk management
The HiScout Data Protection module can be extended to an integrated management system with a common database. A beautiful example of the interaction of the HiScout Basic Protection, HiScout Data Protection, HiScout ISM and HiScout BCM modules: the basic protector becomes active and surveys the processes as well as the required applications. The Emergency Manager is delighted with the collected data and uses it for the Business Impact Analysis. Meanwhile, in the directory of the processing activities, the data protector uses the currently maintained master data to record what data is processed by which application. The basic data protector can incorporate this information into its process analysis to assess the protection requirements.
HiScout technology can be upgraded and is future-proof
The HiScout GRC software is a browser-based multi-user application, which does not require any installation on the client-side. 100% of the development and support are carried out in Germany. The data model and user interfaces of the HiScout Platform can be upgraded and expanded at any time without requiring programming skills, in order to realize individual requirements of our clients. We are in regular dialog with our user groups and in stakeholder forums, and jointly align our development goals with practical needs and future requirements. HiScout Data Protection can be combined with other HiScout add-ons such as HiScout platform can be upgraded and expanded at any time without requiring programming skills, in order to realize individual requirements of our clients. We are in regular dialog with our user groups and in stakeholder forums, and jointly align our development goals with practical needs and future requirements. HiScout Data Protection can be combined with other HiScout add-ons such as HiScout Questionnaire, HiScout Business Logic Engine, HiScout DataExchange and HiScout DocGen to include customised processes, questionnaires, workflows, reports and database connections.
Product Sheet
Find all essential information on the HiScout Basic Protection module here.
Request Now!Synergies
A software for different management systems which saves time and effort.
Work more efficiently!